API Security Testing : Rules And Checklist
September 28th, 2018

One of the most valuable assets of an organization is the data. It is important for an organization to identify the threats to secure data from any kind of risk.
That’s why API security testing is very important. An Application Programming Interface provides the easiest access point to hackers.
To make your data safe from hackers, you should use API security testing and ensure that the API is as safe as possible. If there is an error in API, it will affect all the applications that depend upon API.

An API is a user interface intended for different users.
It is made for a machine running software so that two machines can communicate with each other in the same way that you are kind of communicating with your devices when you are browsing the internet or using certain applications.
Rules For Api Security Testing
Unfortunately, a lot of APIs are not tested to meet the security criteria, that means the API you are using may not be secure.
So, you have to ensure that your applications are functioning as expected with less risk potential for your data. You must test and ensure that your API is safe.
Although, API testing is simple its implementation is hard. Here are some rules of API testing:
- An API should provide expected output for a given input
- The inputs should appear within a particular range and values crossing the range must be rejected
- Any empty or null input must be rejected when it is unacceptable
- Incorrectly sized input must be rejected
Methods Of API Security Testing
Fuzz Testing
It is one of the simple and common ways to test the delicacies in a web service.
It is basically a black box software testing technique which includes finding bugs using malformed data injection.
Fuzz testing does not require advanced tools or programs. Fuzz testing can be performed on any application whether it is an API or not.
You can simply use the command lines like curl and simply send some unexpected value to API and check if it breaks. For example:
Fuzz Testing Numbers: If your API expects numbers in the input, try to send values such as negative numbers, 0, and large digit numbers.
A badly coded application will depend on a certain format, so this is a good way to find bugs in your application.
Fuzz Testing Strings: the best way of fuzz testing strings is to send SQL queries in a criterion where the API is expected some innocuous value.
Undoubtedly, an API will not run any SQL sent is a request
Command Injection
An injection flaw occurs with respect to web services and API when the web application pass information from HTTP request through other commands such as database command, system call, or request to an external service.
For example, you send a request to an API by entering a command ?command=rm -rf / within one of the query parameter.
If the API does not validate the data within that parameter properly, then it could run that command by destroying the contents of the server.
Here we will discuss the ways to test API vulnerabilities.
Operating System Commands in API Requests: You can start with determining the operating system on which the API runs. Generally, it runs on Linux and Windows.
Now, try to send commands within API request that would run on that operating system.
Consider the following example in which the API request deletes a file by name.
| $fn = $_GET[‘filename’]; system(“rm $file”) |
If the user’s request sends a vicious command in the filename parameter, then it will be executed like:
| https://example.com/delete?name=file.txt;rm%20/ |
SQL in API parameters: As similar to operating system command injection, SQL injection is a type of instability that happens when invalidating data from an API request is used in database command. For example
| $name = $_GET[‘username’]; runDbTransaction(“UPDATE user SET username=$name WHERE id = …”) |
An attacker or hacker can easily run database command by making an API request if the input data is not validated properly.
(Un) Authorized Endpoints And Methods
It is very important that an API should authorize every single request before processing it because when the API reveals any sensitive data and allow the users to make damaging actions.
Test For Authentication On All EndPoints: This is one of the ways to test your API security is to set up automated tests in the scenarios such as test authorized endpoints without authorization, test authorized endpoints without authorization and test user privileges.
Test Unhandled HTTP Methods: API that uses HTTP have various methods that are used to retrieve, save and delete data.
The ways to set up a security test for these cases are using HEAD to bypass authentication and test arbitrary HTTP methods.
Parameter Tampering
It takes the advantage of backend sanitizing errors and then manipulates parameters sent in API requests.
According to this, the forms that use type=”hidden” input should always be tested in order to make sure that backend server correctly validates them.
| <input type=”hidden” name=”price” value=”100.00″ /> |
Conceptually, when the user opens his web browser and changes the input valued from 100.00 to 1.00 and submit the form, then the service will be vulnerable to parameter tampering.
API Security Testing Tools
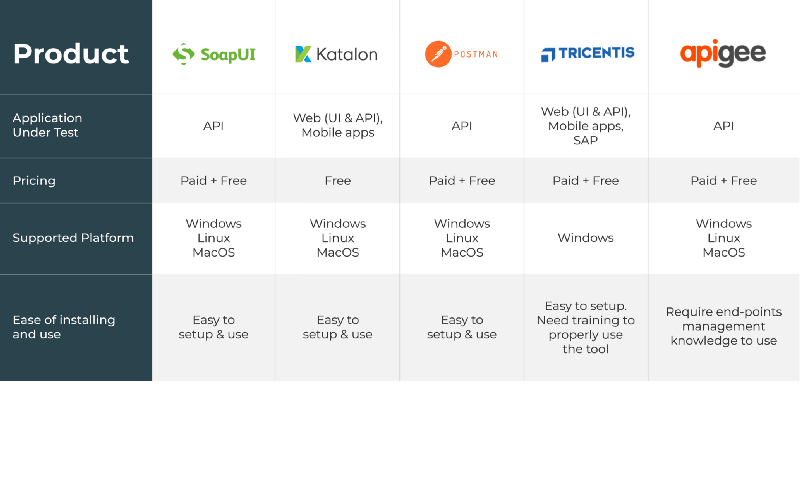 SoapUI
SoapUI
It is a functional testing tool specifically designed for API testing.
It allows the users to test t is a functional testing tool specifically designed for API testing.
It allows the users to test SOAP APIs, REST and web services effortlessly.
Features:
- It runs the test quickly and easily with point & clicks and drag & drop
- The load tests and security scan used in SoapUI can be reused for functional testing
Katalon Studio
It is a free security testing tool for API, web and mobile applications.
It supports both REST and SOAP request with various commands and functionality.
It has the capability of combining UI and API for multiple environments.
Features:
- It supports the data-driven approach
- IT support CI/CD integration
- It supports both SOAP and REST
Postman
It is a security testing tool used to test web services and API.
It was designed to send HTTP requests in a simple and quick way.
Now it has extends its solutions with the native version for both Mac and Windows.
Features:
- It can be run on Linux, Windows, Mac and chrome apps
- It is easy to use REST client
- Rich interface
- Used for automated and exploratory testing
- It doesn’t require learning a new language
- It also has run, test, document and monitoring features
Tricentis Tosca
It is a continuous security testing platform with several benefits and features
Features:
- It supports an array of protocols such as SOAP, IBM MQ, Rabbit MQ, JMS etc.
- API tests can be used across packaged apps, cross-browser, mobile etc.
- It reduces the time of regression testing
Apigee
It is a cross-cloud API security testing tool which allows the users to test and measure the performance of API.
Features
- Powered by Javascript.
- It allows design, monitor, scale and deploys API.
- Identify performance issues.
- Create API proxies.


 Software Testing Events
Software Testing Events App Testing
App Testing Web App Testing
Web App Testing Game Testing
Game Testing Automation Testing
Automation Testing Load Testing
Load Testing Security Testing
Security Testing Performance Testing
Performance Testing Hire a Tester
Hire a Tester